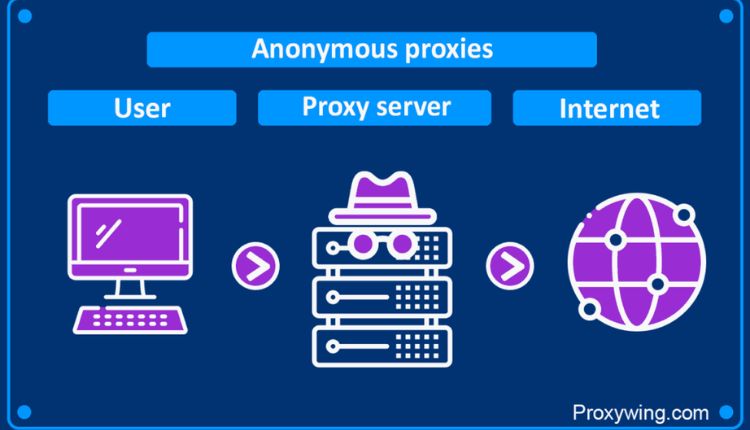
Online privacy has become a serious priority for organizations that rely on stable digital operations. Secure routing and concealed identity now influence performance, access, and data protection. Anonymous proxies step into this space as structured tools that keep network activity discreet and controlled.
A high anonymous proxy stands out as a refined option for users who need deeper identity concealment across networks. This type of solution hides IP details and request headers with precision. Digital tasks continue with greater confidence when exposure risks stay low.
Transparent, Anonymous, and Elite Proxy Categories
Proxy services fall into clear categories based on how much data they reveal to destination servers. Transparent proxies pass along original IP information, which suits filtering or caching tasks but offers no privacy shield. Anonymous proxies hide user IP addresses yet still identify themselves as intermediaries.
Elite or highly anonymous proxies conceal both the user identity and the proxy presence. Requests appear to come directly from standard users without extra proxy headers. This higher level of anonymity reduces detection risks across sensitive operations.
Functional Differences That Shape Use Cases
Each proxy type serves a distinct purpose across digital workflows. Transparent options support monitoring and network control within internal systems. Anonymous and elite variants fit research, automation, and location-specific access needs.
Elite solutions provide the highest level of disguise for sessions that demand continuity. Platforms treat traffic as a natural activity due to the absence of proxy signals. Stable interaction becomes easier when systems recognize requests as standard user behavior.
Core Advantages of High Anonymity Solutions
- IP masking prevents exposure of real device addresses during online activity.
- Header suppression removes proxy identifiers from server requests.
- Session stability increases due to consistent identity presentation.
- Platform trust improves when traffic appears natural and localized.
These characteristics define the strength of a high anonymous proxy in professional environments. Operations that depend on reliability gain an extra layer of protection. Network behavior remains smooth and predictable under scrutiny.
Performance and Stability Across Regions
Anonymous proxy networks distribute requests across multiple IP addresses. Traffic spreads in a balanced manner, which prevents strain on single endpoints. Response times remain steady even when operations span several regions.
Location-based access becomes more reliable under high anonymity conditions. Regional IP alignment allows content testing and localized interaction without sudden disruptions. Consistent routing ensures dependable task completion.
Practical Reasons to Purchase Anonymous Proxy Services
- Long-term projects gain stability through dependable IP rotation.
- Brand monitoring stays accurate with region-specific visibility.
- Automation tasks perform better under consistent identity settings.
- Account management improves with reduced verification triggers.
Organizations choose to buy anonymous proxy tools to support sustained digital strategies. Reliable anonymity helps maintain access to platforms with strict security filters. Controlled routing enhances both efficiency and predictability.
Cost Efficiency Through Reliable Operations
Interrupted tasks lead to wasted resources and repeated processes. Stable proxy services reduce downtime linked to connection issues. Investment in dependable anonymity leads to smoother workflows.
Maintenance needs decline when systems encounter fewer access barriers. Operational planning benefits from predictable network behavior. Efficiency grows as disruptions decrease.
Strategic Value of Premium Anonymous Infrastructure
Premium anonymous proxy services provide refined control over session handling and IP pools. Administrators adjust routing preferences and identity settings with precision. Structured control ensures alignment with operational requirements.
Integration with automation platforms remains straightforward. Businesses that buy anonymous proxy solutions gain compatibility across tools and systems. Seamless deployment supports structured and repeatable digital tasks.
So, anonymous proxy categories serve distinct roles across digital operations. Highly anonymous solutions deliver deeper privacy, stability, and access reliability. Investment in advanced anonymity supports secure and consistent online performance.